What is ‘NTLM Authentication’ in Windows 10?
In this post, we are going to discuss on “How to disable NTLM Authentication Windows 10”. You will be guided with easy steps to do so. Let’s starts the discussion.
NTLM Authentication in Windows 10: NTLM stands for New Technology LAN Manager. It is package for security protocols offered by Microsoft to authenticate users’ identity and protect the integrity and confidentiality of their activity. This technology relies on Challenge-response protocol to confirm the user without them to submit a password.
NTLM Authenticates users using a challenge-response mechanism. These process consists of three messages including Negotiation message from the client, Challenge message from the server and Authentication message from the client. However, due to known vulnerabilities, NTLM remains widely deployed even on new systems in order to maintain the compatibility with legacy clients and servers.
NLTM is still support by Microsoft, it has been replaced by ‘Kerberos’ as the default authentication protocol in Windows 2000 and subsequent Active Directory (AD) domains. If you are not aware, ‘Kerberos’ is authentication protocol replaced NTLM as the default/standard authentication tools on Windows version 2000 and later. The main difference between ‘Kerberos’ protocol and ‘NTLM’ protocol is whether passwords are hashed or encrypted. NTLM relies on ‘Password hashing’ – one-way function that produces a string of text on an input file while ‘Kerberos’ relies on encryption – two way functions that scrambles and unlocks information using encryption & decryption keys.
Also, NTLM relies on three-way handshake between client and server to authenticate user while Kerberos relies on two-way process that provides a ticket grating service or key distribution center. NTLM protocol was subject to several security risks and known security bugs or issues related to password hashing and salting.
NLTM protocol stores password on the server and domain controller are not ‘salted’. It means you can’t add any random string of characters to the hashed password to further prevent it from cracking techniques. This vulnerability could allow attackers or cybercriminals attempts to crack password through multiple login attempts, and due to weak or common password, they could successful in accessing the account.
Problem with NTLM protocol:
- Stored password Hash in memory of LSA service can easily be extracted using different tools like mimikatz, and then the hash password may be used for further attacks
- Weak or common passwords are another reason for NTLM protocol problem
- The absence of mutual authentication between server and client that results in data interception attacks and unauthorised access to the network resources.
- Other NTLM vulnerabilities or issues.
How to disable NTLM Authentication Windows 10 using Group Policy Management Editor?

First of all, the domain administrator requires to make sure that NTLM and LM protocols are not allowed to be used for authentication in domain. You can set the preferred authentication type using domain (or local) policy.
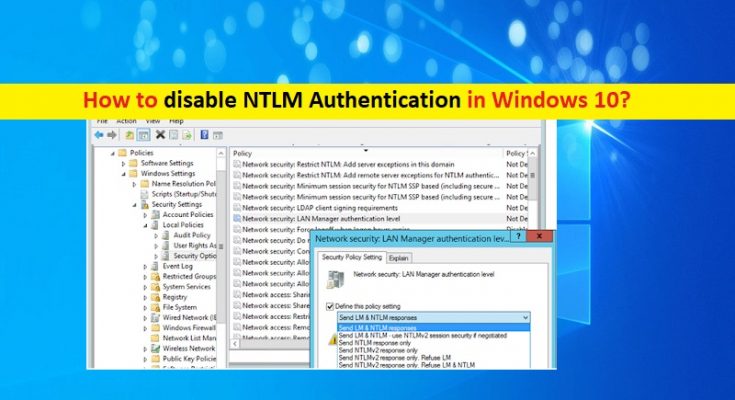
Step 1: Press ‘Windows + R’ keys on keyboard, type ‘gpmc.msc’ in the opened ‘Run’ dialog box and hit ‘Ok’ button to open ‘Group Policy Management Editor’
Step 2: Go to ‘Computer Configurations -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options’
Step 3: Find ‘Network Security: LAN Manager authentication level’ policy, and double-click on it
Step 4: Select ‘Send NTLMv2 response only. Refuse LM & NTLM’ option under ‘Send LM & NTLM responses’ section/dropdown to reject all LM and NTLM requests.
How to disable NTLM Authentication Windows 10 using Registry Editor?

Step 1: Press ‘Windows + R’ keys on keyboard, type ‘regedit’ in the opened ‘Run’ dialog box and hit ‘Ok’ button to open ‘Registry Editor’
Step 2: Navigate to following path
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa
Step 3: Now, right-click on empty space in right pane and select ‘New > DWORD’ and name it to ‘lmCompatibilityLevel’, set its value to ‘0 to 5’ and hit ‘Ok’ button to save
Step 4: Here, option 5 As value data correspond to ‘Send NTLM response only, refuse LM and NTLM’. Apply the changes.
How to enable NTLM Authentication Audit Logging?
You should make sure there are no apps left in the domain that require and use NTLM, before disabling NTLM completely in domain and switching to ‘Kerbeors’ protocol.
Step 1: Open ‘Group Policy Management Editor’ using above methods, and go to ‘Computer Configurations -> Policies -> Windows Settings -> Security Settings -> Local Policies -> Security Options’ path
Step 2: Find and enable ‘Network Security: Restrict NTLM: Audit NTLM Authentication in this domain’ policy, and set its value to ‘Enable All’
Step 3: Repeat the same step to enable ‘Network Security: Restrict NTLM: Audit Incoming NTLM Traffic’ policy
How to check events of using NTLM Authentication?
You can see the NTLM Authentication appear in the application and services logs.
Step 1: Go to ‘Services Logs’ and go to ‘Microsoft > Windows’
Step 2: Take NTLM section of Event Viewer. Now, you can analyze the events on each server or collect them to central Windows Event Log Collector.
Step 3: Find out the applications that are using NTLM in domain, and you need to switch them to use ‘Kerberos’ possibly using SPN.
How to restrict NTLM in Active Directory Domain completely?
The authentication without NTLM will work differently for each applications in our domain, we can add user accounts to ‘protected users’ Doman group. Once verified, you can completely disable NTLM Authentication in your Windows domain.
Conclusion
I am sure this article helped you on How to disable NTLM Authentication Windows 10 with several easy steps/methods. You can read & follow our instructions to do so. If the article really helped you, then you can share the post with others to help them. That’s all. For any suggestions or queries, please write on comment box below.