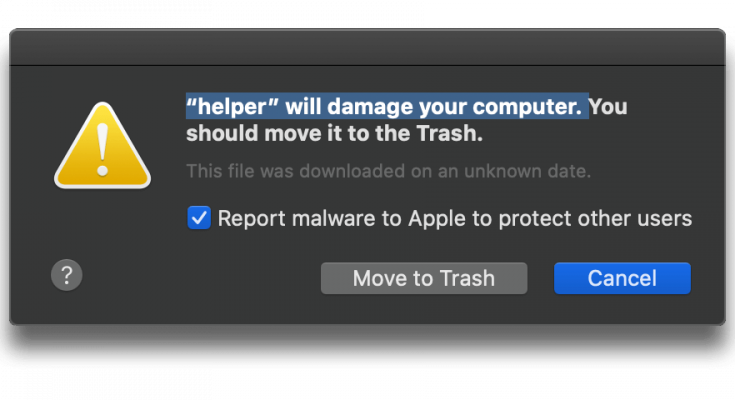
* will damage your computer Removal Guide
It is almost impossible to work smoothly on a Mac OS X infected with an adware. They are spam and rather digital threats for your data security and smooth performance of the work-station. Many of them are termed as potentially unwanted program (PUAs) simply because they attack the targeted Mac silently. Its initial symptoms could be excessive ads and pop-ups and spoofed up alerts. These pop-ups and alerts redirects over other shady websites or display banners for useless services and offers that don’t exist. Most of these alerts are in the form of * will damage your computer Mac where * could be replaced with DominantPartitiond, ProtocolStatus, StandardBoostd, OperativeMachined, ActivityInputd, CleanParameterd, ElementaryTyped, ManagerAnalogd and so on.
All these are adware strain for Mac OS X which has been noticed in Mac Big Sur as well and their distribution has been noticed a sudden spike recently. The alert message depends on number of factors such as Mac OS version, IP address, geo-location, installed software, browser and so on. You would notice some basic changes in the browser settings such as preferred search-engine provider, new-tab URL settings, homepage and so on. You are manipulated to use a bogus search provider which is a copycat of reputed search-engine such as Google, Yahoo or Bing. It irritates with transitional URLs which are part of big advertising network.
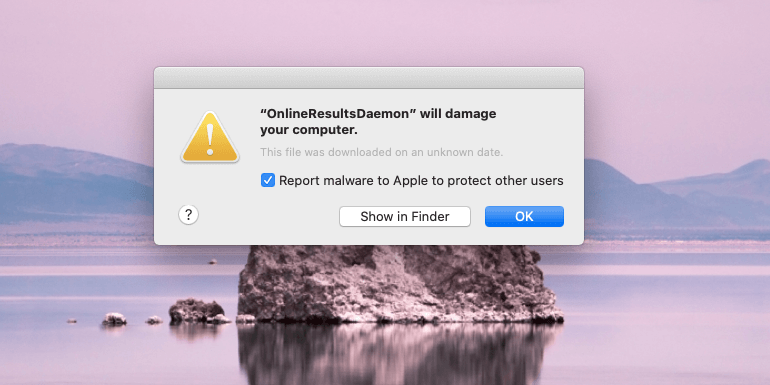
If you notice * will damage your computer Mac regularly, there is bound to be some suspicious browser extension that interferes in the way webpage content is displayed to the users. These add-ons or extensions are capable to execute scripts so that customized ads and pop-ups could be triggered based on the browsing history of the users. The pop-ups or alerts are totally aligned on the user’s interests. This signifies other proof for privacy encroachment properties of a PUA. The sensitive data may get exposed and this often leads to huge financial losses for the users.
In the latest MacOS Big Sur 11.2, the adware pop-ups or PUA alerts is flagged as potential threat. The pop-ups are displayed as “*will damage your computer”. The dialog recommends removing the PUAs or programs that are causing such issues. However, when you click on the embedded button to remove the culprit application, nothing happens. Rather, an additional pop-up appears on the screen that tells that the application is in use and is cannot be uninstalled. The system warning pop-ups appears continuously and starts to irritate very badly. In this kind of situation, the best and probably the only solution that works is to scan the PC with a powerful anti-malware tool that has strong scanning algorithm and programming logics.
Special Offer (Macintosh)
Mac users if infected by adware, can try a suggested application to do scan and check if all malicious files and entries are completely removed.
More Details on * will damage your computer Pop-ups on Mac OS X
The Mac OS X has a security feature named as “GateKeeper” that verifies the processes that is to be executed. * will damage your computer pop-up is the result of this feature that alerts users about the potential damage caused to the operating system. Whenever there is suspicious process or binaries get executed this kind or warning pop-ups appears.
Some of the known processes flagged by Mac Big Sur has been listed below.
- Safe Surf FinderDaemon
- SearchConsoleDaemeon
- SearchSystemsDaemon
- SkilledObjectd (Feb 2021)
- SorimbrsecDaemon
- ActivityInputd (Mar 2021)
- AnalyzerWindowd (Feb 2021)
- CleanParameterd (Feb 2021)
- ConfigTyped (Feb 2021)
- DigitalDataSourceDaemon
- DominantPartitiond (Mar 2021)
- ElementaryTyped (Feb 2021)
- ExtendedSprintd (Feb 2021)
- HP Scanner 3
- HP Utility / HP Utility 3
- InitialProgramd (Feb 2021)
- InitialSkilld (Feb 2021)
- Kanbanier
- LauncherSetup (Feb 2021)
- libecomlodr.dylib
- ManagerAnalogd (Feb 2021)
- Nearwoodce
- Ocensmail
- OnlineResultsDaemon
- OperativeMachined (Mar 2021)
- OriginalModuled (Feb 2021)
- PDE.Plugin
- PenTabletSpringboard
- PlaybeatTrial
- ProtocolPort (Feb 2021)
- ProtocolStatus (Feb 2021)
- Receiver Helper
- RecordMapperd (Feb 2021)
- SpiderOak
- StandardBoostd (Feb 2021)
- StandartProductd (Feb 2021)
- SymLicensing.framework
- TechFunctionSearchDaemon
- TituricsecDaemon
- TrustedAnalogd (Feb 2021)
- Unithandlerd (Feb 2021)
- Fax.Backend
- HerculesLookupDaemon
- Hmopt
- HPDeviceMonitoring.framework
- hpdm.framework
- hpPostScriptpde.plugin
Most of these processes and executable are associated with adware and PUAs. They find difficulty to bypass the operating system checks and hence are categorized under privacy and security issues. In some cases, the obsolete version of reputed and genuine products that lacks the security update also triggers such as alerts and pop-ups. Some of them have been discussed below.
“Service Records will damage your computer” pop-up alert
“Service Records” is the process used by “Citrix Receiver” which is a workspace visualization tool. It was replaced by a new app named as “Citrix Workspace” in 2018. So, if you use the earlier variant, the Mac OS will trigger the alert error. So, if you uninstall the older variant and replace it with the latest version, the pop-ups will automatically get stopped.
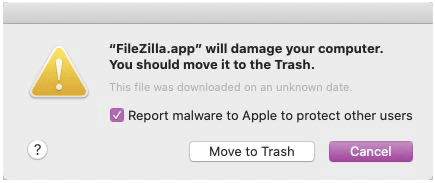
“FileZilla.app will damage your computer” warning
FileZilla is a popular application used for file transfer between PC and a server. If there is an Out-of-date built of FileZilla, the Mac OS X treats it’s execute as threat. So, possibly if you delete the current version and install the most recent version from the official vendor website, the problem will get solved.
“Steuern2016 will damage your computer” pop-up warning
Unlike the two processes discussed above, Steuern2016 doesn’t belong to any genuine application and rather it is a part of an adware. It is used for webpage redirections and to make unwanted changes in the browser settings. The appearance of this alert is only possible if the associated application gets detected and is removed. The easiest way is to scan the PC with a malware security tool.
“Sibelius6 will damage your computer” message
Sibelius6 is a process associated with Sibelius6 music notation tool that allows the users to edit, create and print music. It is not dangerous but reports reveal that its previous version may have security loopholes for malware exploitation. Hence, Mac OS X “Gatekeeper” detect this app as PUA and hence triggers pop-up alert. Again if you replace the latest Sibelius 6.1, problem could be fixed. You need to detect all instance of Sibelius6 file and remove them. Additionally remove the files form trash as well and then download the fresh version from its official website.
In recent times, probably in last year or two, the problem with the Mac OS X malware is getting worse. They are not safe as they used to be. If you think that it is only the Windows users who have to take precautions then you are totally on a wrong path. According to multiple surveys by cyber-experts, the number of Mac malware is outpacing PCs. Users are not safe just because they are using Mac OS X. “Apple Company” itself are now resentfully admitting that Mac OS X can get infected with Trojan, Adware, PUPs and so on.
〈How adware can infect Mac OS X based PC?〉
Spam Emails:
The targeted potential victims are tricked to downloaded harmful files. You may receive a mail with an attached file claiming that it is a delivery receipt, invoice or tax refund documents. It may say to open the attached file to get items delivered to you or to get money. Simply, opening the attached file will end up installing malware. Such spam emails usually have spelling or grammatical errors. They may asks you to update your personal details and provide a link to do so.
Bundled with Other Software (Bundling)
In many cases, the users face issues right after they have installed any program in the work-station. This directly means that some malware can get installed along with any other software. This includes application from third-party platforms and peer-to-peer file sharing networks. They can download an extra toolbar or extension categorized as PUPs and their only aim is to show excessive ads and pop-ups. In researches, it got notice that the program that generates software keys (keygens) often install other doubtful application along with them. It is important that you carefully read with you are installing. Download any software only from a trusted source.
Through Hacked Webpages
If there is software vulnerability then this can be utilized by the Malware to infect your PC. If you visit any malicious websites, such loopholes can easily be installed to download harmful files without your knowledge. Hence you should always get the latest updates for the software you use.
Infected Removable Drives
Originally, the most popular way to insert malware was through any external storage device. Recently, the firmware of a USB stick is used to doing the same. The malware are hidden under the firmware and it is very difficult to detect. Additionally, a USB, external hard-disk or drives, CDs, DVDs etc. may contain unsafe files attached to them.
Not Using Internet Security Program or Anti-malware Tool
Even today in this digital world, there are many users who don’t understand the importance of PC security software. It is very important to have a proper protection for all your devices. The business in the malware world is booming and you could definitely be their next victim if you are not careful. As an tech savvy individual, you know exactly what to look for as far as malware infection is concerned but knowing that you can even get infected with malware even when you visit a compromised website. It is extremely important to have a proper Internet security program or anti-malware application in the work-station.
〈Why MacKeeper?〉
If you are unaware, we tell you that your device has built-in antivirus tool already installed on your system to protect the system from PC threats and viruses. So, in such a case there is no need of any third party antivirus tool. However, using MacKeeper and other such tools become necessary because some PUAs like infection can easily bypass the built-in security and install on the system. After the installation, they disable the firewall alerts and make the completely vulnerable for other malicious malware infection. The default AV tools could not detect the entry because a lot of investment is done by crooks in making such applications appear legitimate upon detection.
MacKeeper is helpful in this case. It is especially tuned up for protecting the system from any potentially unwanted applications. Also, it can check the system for other potentially dangerous malware like Trojan, Ransomware, worm and so on. Hence, it will ensure that these threats could not lead personal data leakage. Not only that, it will tune up the performance of the system by removing junk, duplicates and useless applications, Mac’s memory and log-ins items and so on.
MacKeeper: Download/ installation guide
- Click on below button to download MacKeeper file within the system,
- When the installation process is completed, a file named MacKeeper.dmg or MacKeeper.pkg will be downloaded within the system,
- Go to the Finder and Select Downloads to see this file,
- Then, open it to begin installation process and follow the on-screen instructions to finish the process.
Use the program’s free/ paid version
MacKeeper has certain features that the users can try once for free to see how it works. However, the app’s features will not work until you purchase the license version. So, purchase the full license version of the program if you want to keep all the benefits of the app.
Steps to find activation code:
- Open the program,
- Click on green unlock Full version in the bottom-left corner of the page,
- Then choose your Plan
Once the purchasing is proceeded, you will get the 16- digit activation code on the screen. This code will also be sent to the email address you provided. When you have the Activation key, follow the below steps to get access to the full features of the app:
- Open the program,
- Click MacKeeper and choose Enter Activation Code,
- Paste the activation code in the MacKeeper Window and then click Apply
In the process, you will be asked for the Mackeeper account. If you don’t have, create one. If have, log-in in to this and complete the activation process.
MacKeeper setup guide:
- Open the program and click on Start Full Scan,
- Then, select Fix Items Safely option,
- Follow the setup prompts next to this,
- Click on Done option when all suggestions are completed.
This is the required steps to complete the MacKeeper setup. Next, launch the scan and check for system for adware and all its malicious components for their removal.
User guide to remove adware using MacKeeper:
- Open MacKeeper,
- Select Antivirus on the left sidebar, and then click on Launch Antivirus,
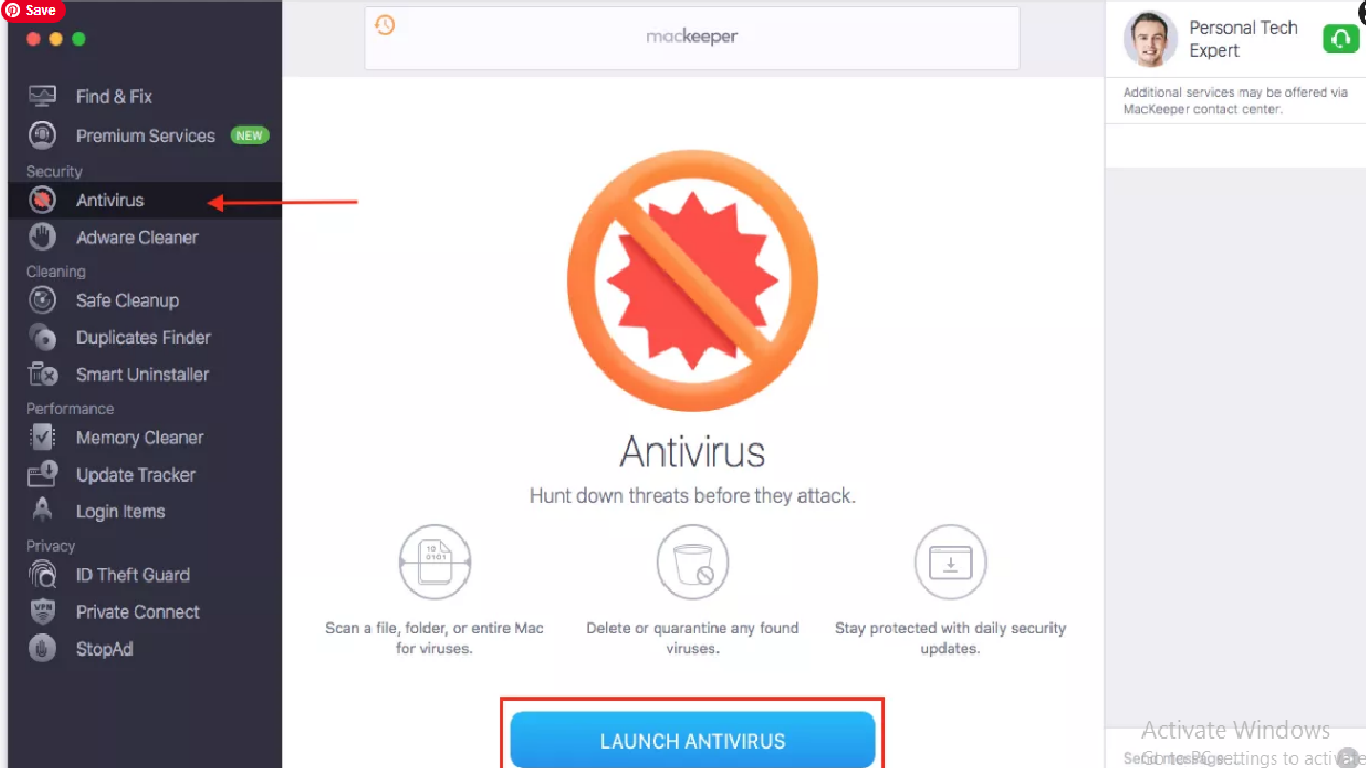
- Antivirus will start enabling (the process takes few seconds to start),
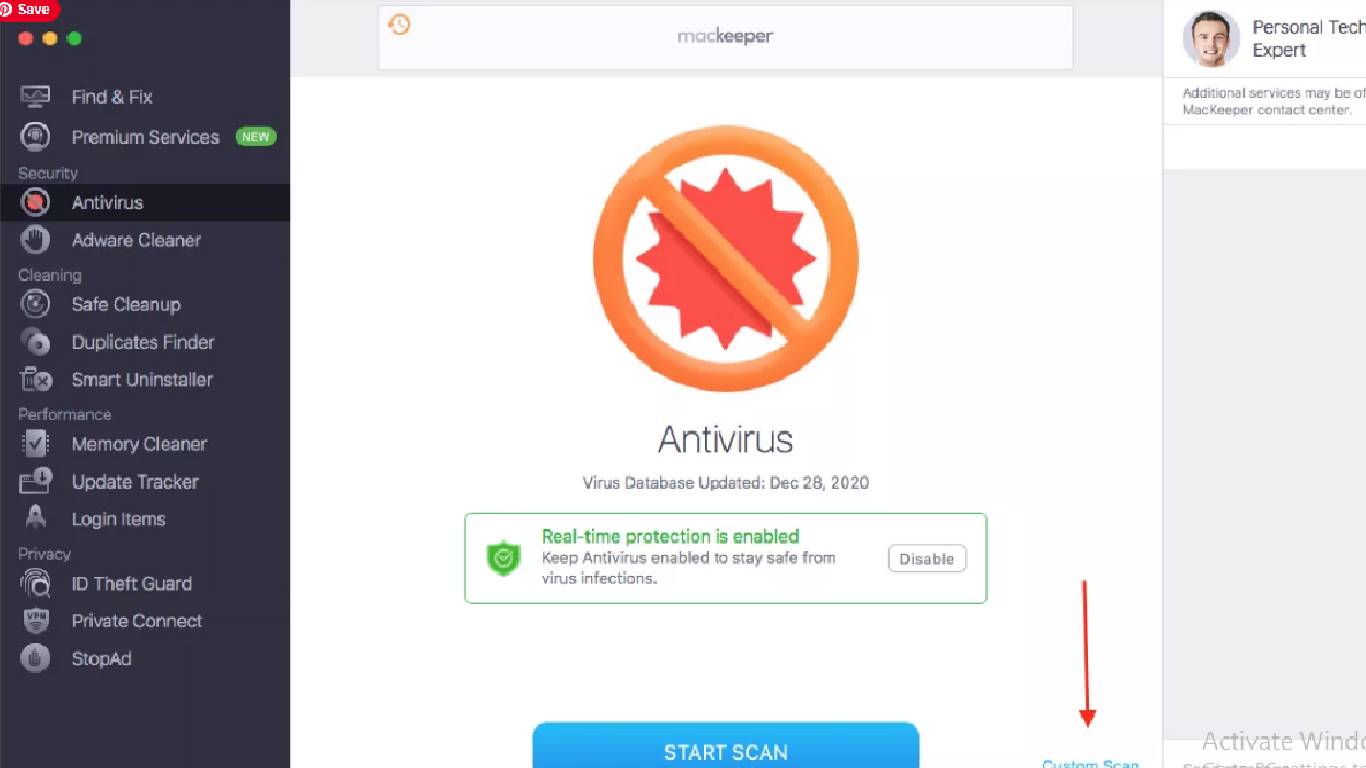
- Click on Custom Scan to check for specific folder or USD drive,
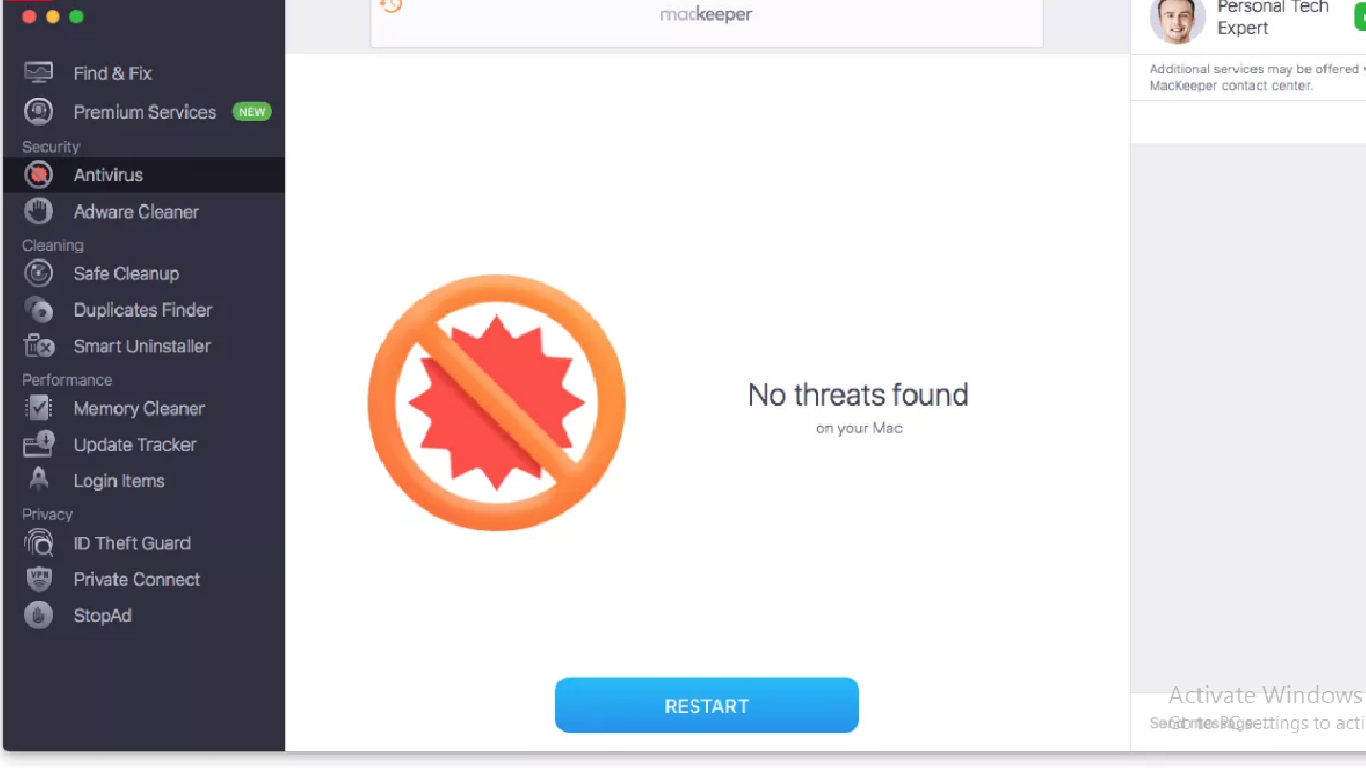
The software scans for all viruses, malware, Trojans and other major threats on the system and when the process is complete, it shows the result on the screen. If your Mac is safe, you will see the following screen:
However, if the scanning result shows any malicious detection, click on the items that are malicious and remove those by clicking delete button (or you can Quarantine to isolate them from infecting the device).
Next to this, choose Adware Cleaner option in Antivirus Section, and click Open (the software will then scan the system for adware, browser hijacker and other potentially unwanted applications):
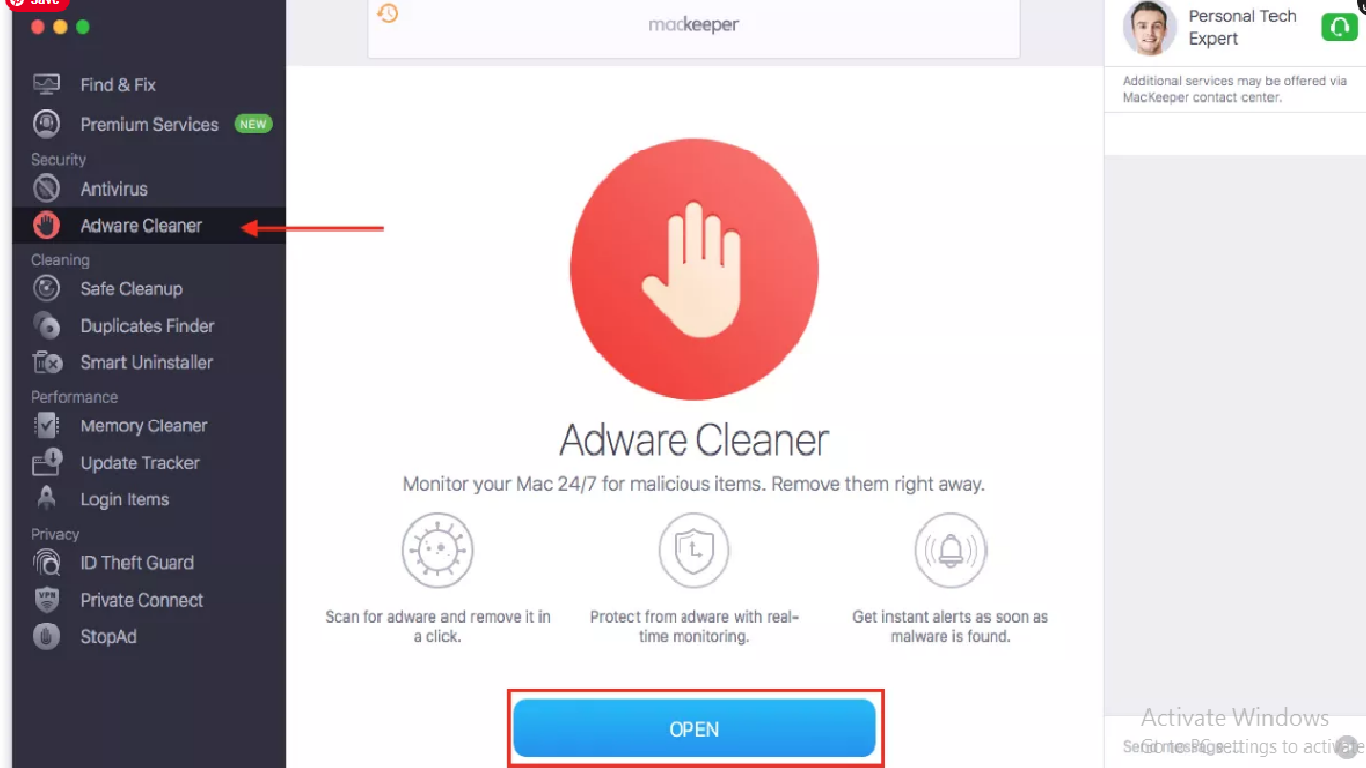
- click on Start Scan button,
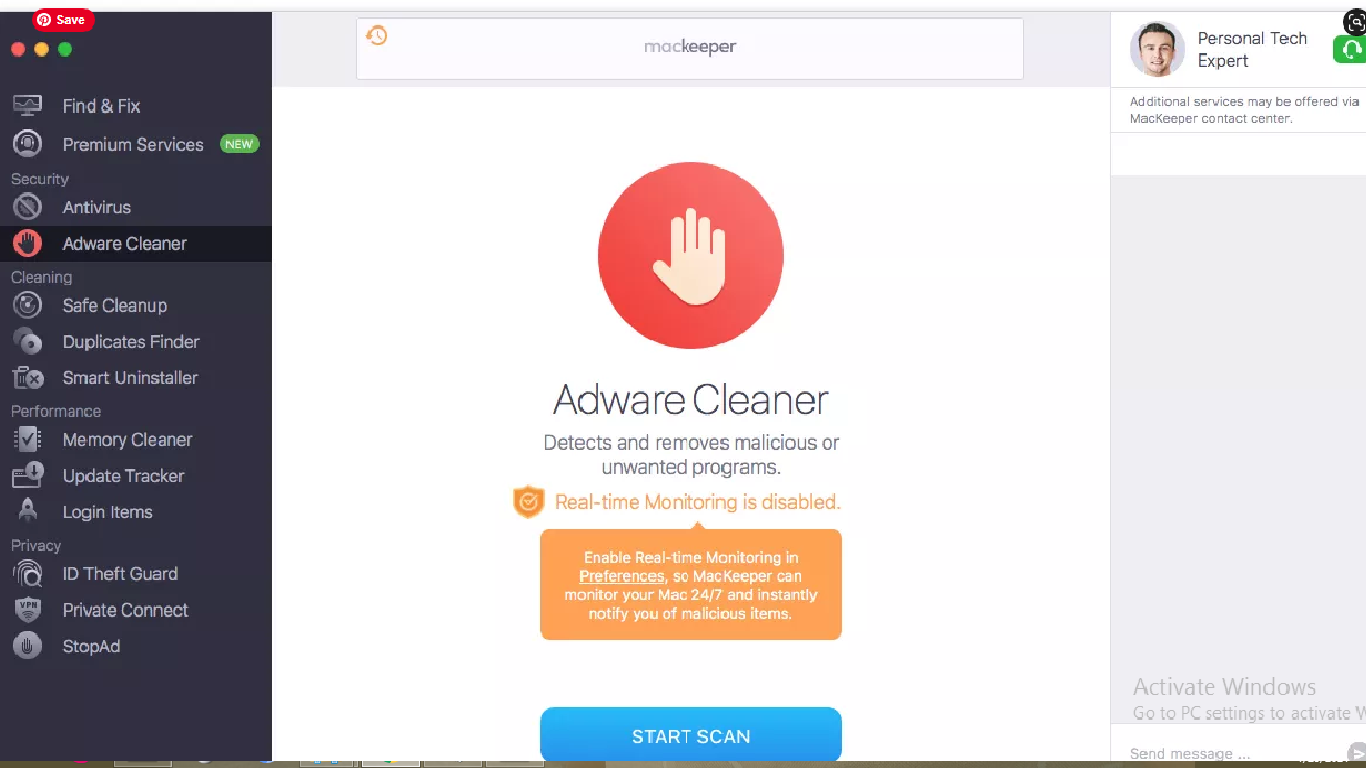
- Once scanning process is completed, the program shows the scan results on the screen. Take the immediate actions.
Special Offer (Macintosh)
Mac users if infected by adware, can try a suggested application to do scan and check if all malicious files and entries are completely removed.
〈Remove adware using the following steps:〉
⇒ Delete adware from MacOS X
⇒ Erase adware from Google Chrome
⇒ Remove adware from Mozilla Firefox
⇒ Delete adware from Safari
→ Get rid of adware from Mac OS system
To completely un-install adware, you need to delete all its related components by the steps below:
- Click on Go> utilities,

- Double-click on the Activity Monitor,
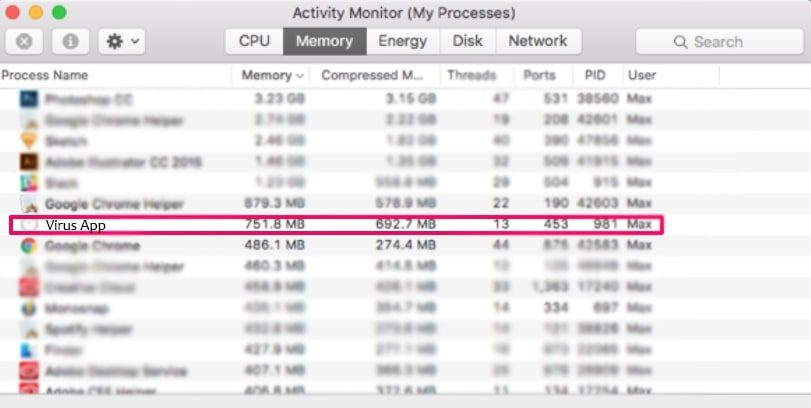
- Check for adware related processes in the opened window,
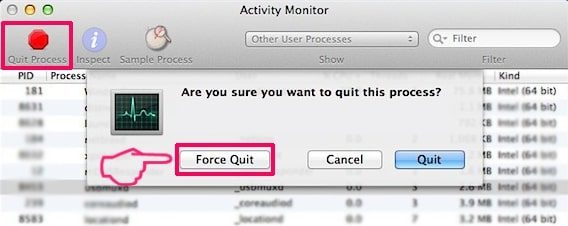
- Forcibly quit these process by clicking Force Quit option
- Then, click on Go> Applications to open Applications Menu,
- Under this menu, look all suspicious files or apps with name identical to adware and move all of them to trash by clicking right-click and selecting Move To Trash option,
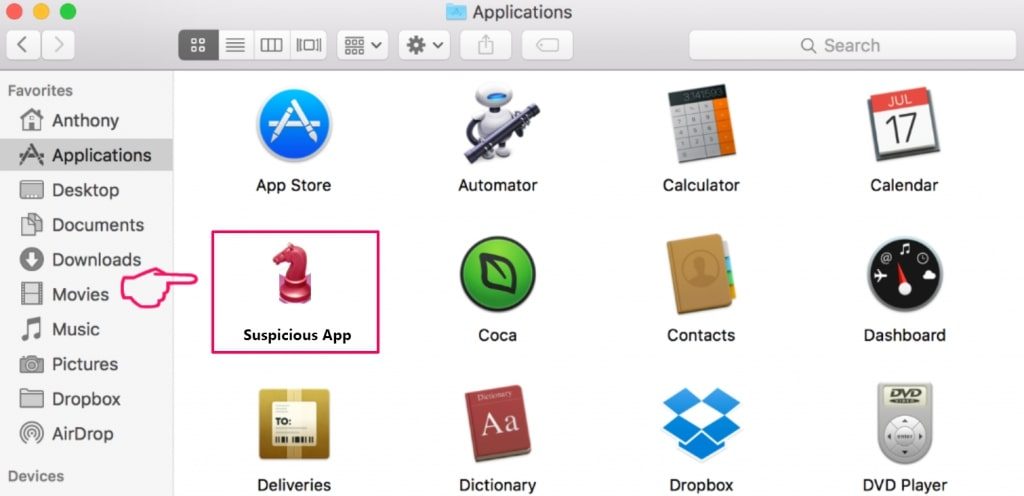
- Next to this, select your account and click on Log-in items preference.
A page appears with a list of the apps that automatically start with your log-in. Check for the suspicious adware files and stop them to run automatically by clicking “Minus” icon next to it.
Now, look for the left-over files by the following sub-steps:
- Click on Finder and search with the name you want to remove on the search bar,
- Change the drop down menus with “System Files” and “Are Included” (by this, you will be able to see all associated files with the application you want to remove. The list might include some files which are not related to the app and be careful about it),
- Then, make selection to the files and drive then to Trash
In case, you can’t find adware and related files and objects in your Applications or other places as shown above, you should check the system on Libraries:
- Click Go> Go To Folder,
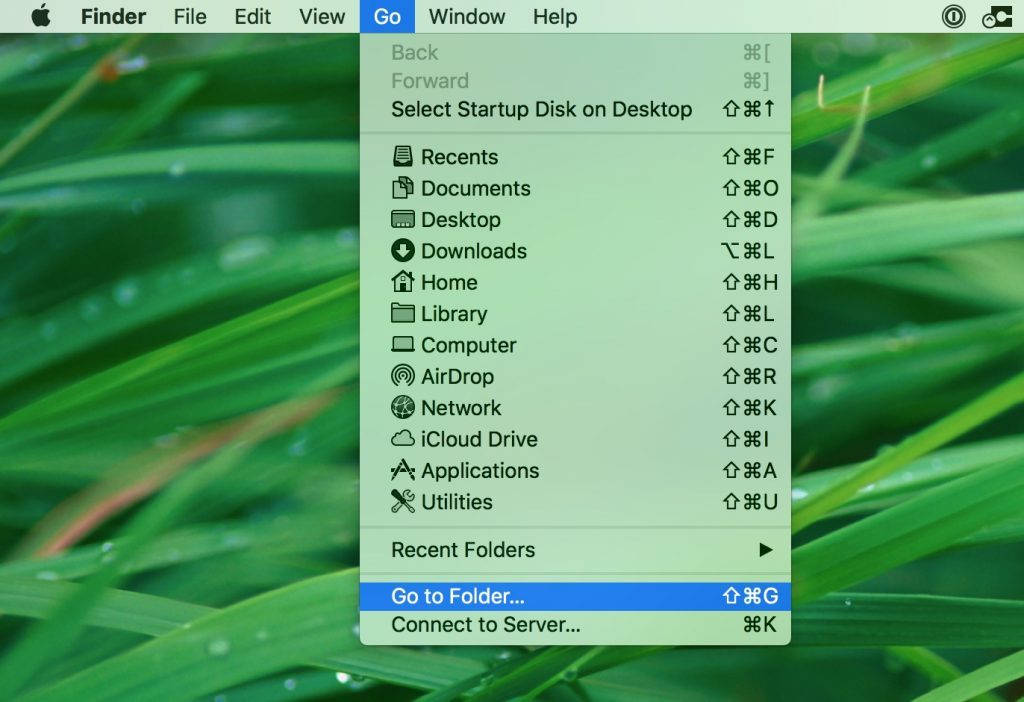
- Type “/Library/LauchAgents/” and press Ok,
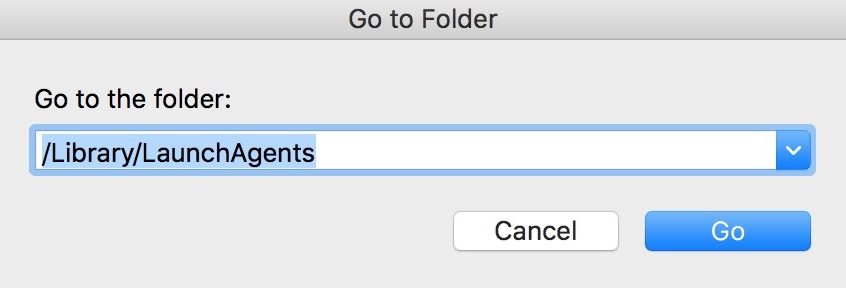
- Delete all the files related to adware. Do not delete any such files that you think not associated with the virus.
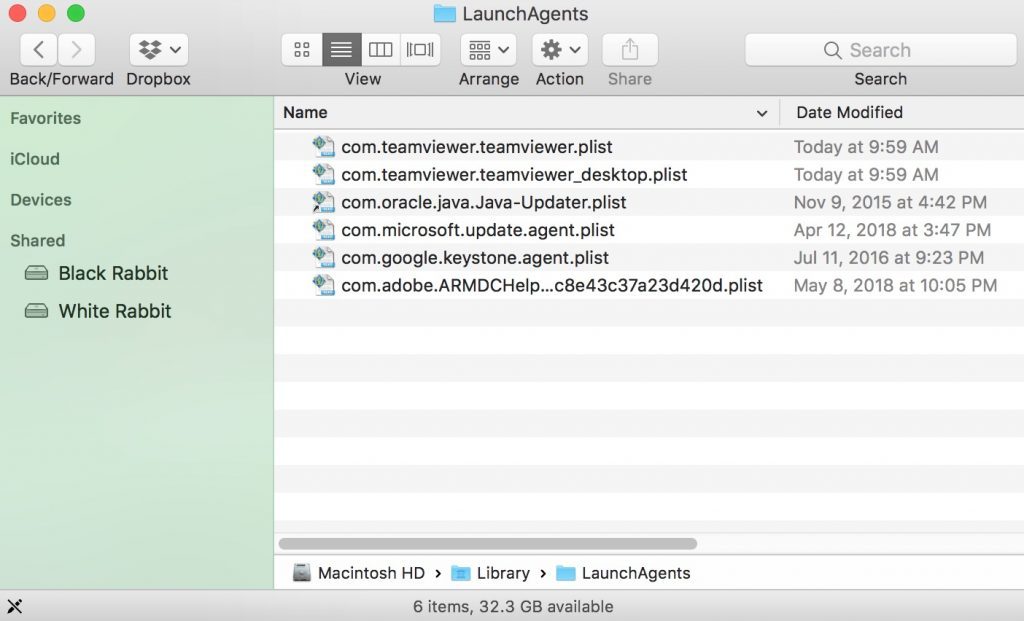
- Repeat the same process to check for adware related components in other Library directories:
→ ~/Library/LaunchAgents
/Library/LaunchDaemons
→ Erase adware from Google Chrome
Delete malicious extensions:
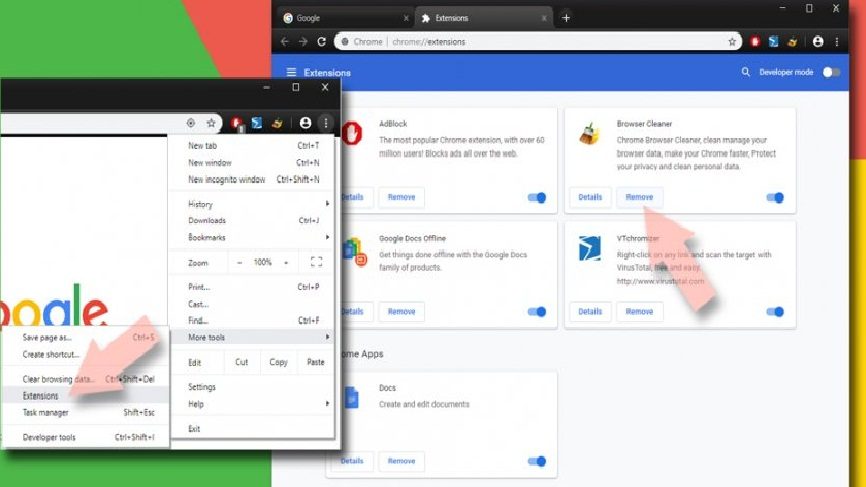
- Open the Google Chrome and click on the drop menu,
- Move the cursor over More Tools and select Extensions,
- In the newly opened window, check for all suspicious plug-ins related to adware and remove them by clicking Remove button.
Clear the browser cache and web data:
- Click on Menu,
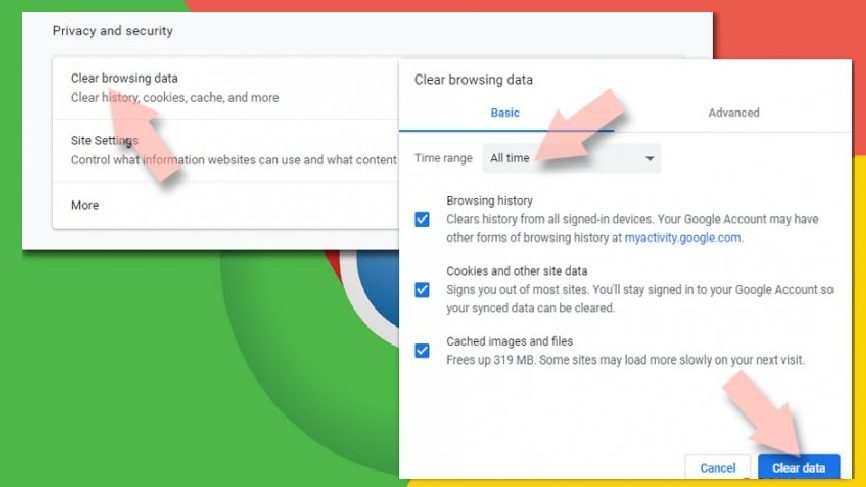
- Select Settings,
- Under the privacy and security, select the option says Clear browsing data,
- Click on Browsing history, Cookies and other site data and also the Cached image and files to make selection,
- Then, delete the selected items by clicking the Clear data
Restore the browsers’ homepage:
- Click on Menu and choose Settings,
- In the On Startup section, look for the suspicious adware site,
- Then, click on Open a specific or set of pages, select three dots and click on Remove
Reset Google Chrome:
Completely reset the web browser to automatically remove all suspicious elements associated with adware:
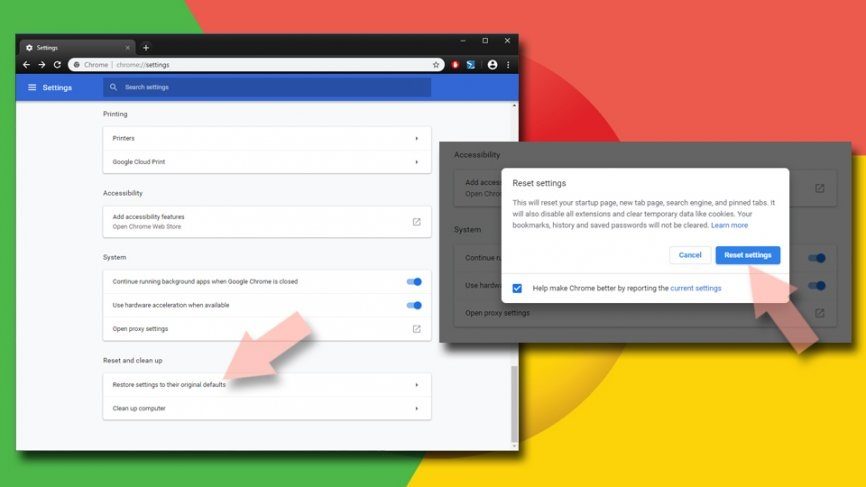
- Click on Menu and go to the Settings,
- Click Advanced,
- Scroll down to find Reset and clean up,
- In this section, click on Restore settings to their original defaults,
- And finally, confirm with clicking on Reset settings.
→ Remove adware from Mozilla Firefox
Remove malicious extensions:
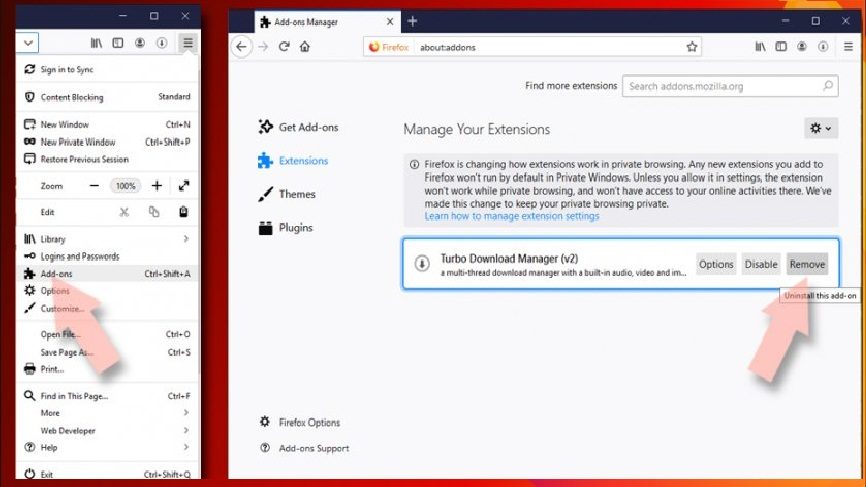
- Open Firefox and click on Menu (by clicking three horizontal lines at the top right of the page),
- Select Add-ons, select all plug-ins related to adware and remove them
Change the homepage:
- Go to the Menu and choose Options,
- Under the Home option, enter the preferred site that you want to open each time when you newly open the web browser
Clear cookies and site data:
- Click on Menu and choose Options,
- Under the Privacy and Security, find cookies and Site Data,
- Click on Clear Data,
- Select Cookies and Site Data and also the Cached web content and then click
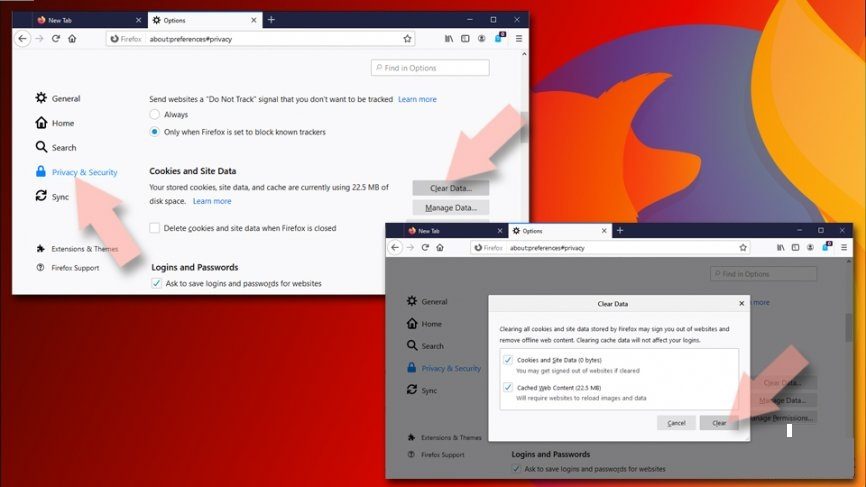
Reset Firefox:
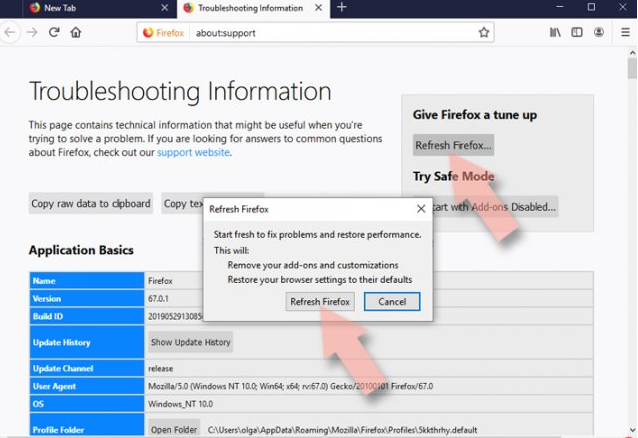
- Open the web browser and click on Menu,
- Go to Help section and find Troubleshooting information,

- Click on Refresh Firefox… under the Give Firefox a tune up section,
- Then, you will have a pop-up shows to the screen, confirm with clicking on Refresh Firefox to complete the process.
→ Delete adware from Safari
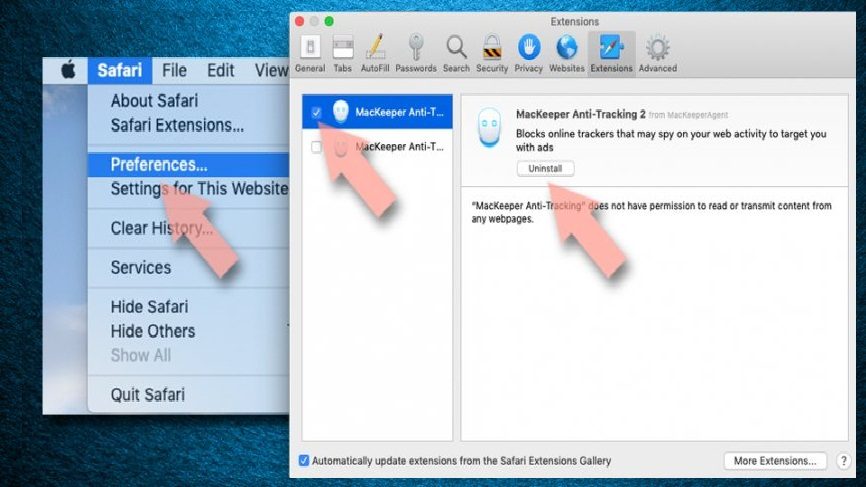
Remove unwanted extensions:
- Click on Safari and go to preferences,
- Pick Extensions in the opened window,
- Then, select the unwanted extensions related to adware and click on Un-install.
Clear cookies and other website data:
- Go to the Clear History option under Safari,
- In the Clear section, pick all history,
- And Confirm with Clear History.

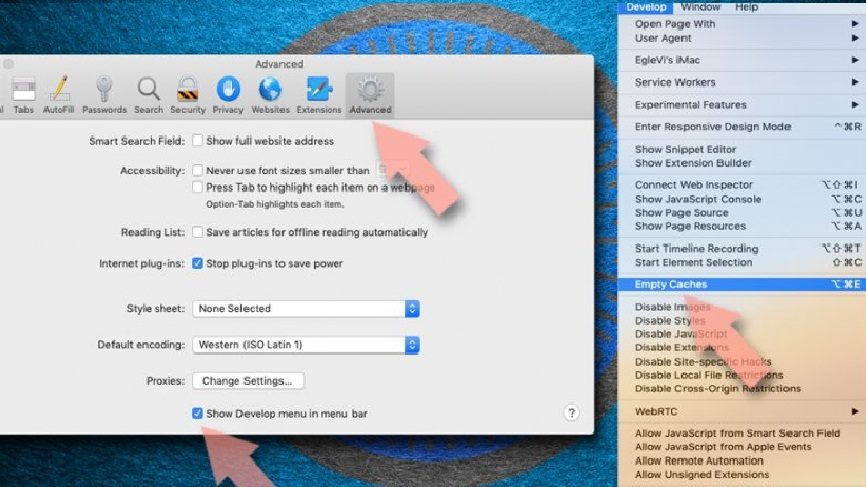
Reset Safari:
- Go to the Preferences by clicking Safari> Preferences,
- Click on Advanced tab,
- Select Show Develop menu,
- Click Develop and then select Empty Caches
After completing these steps to remove adware and associated components from all web browsers installed, you should run a full system scan using some reputable antivirus tool that will help you in getting rid of all the registry traces for the infection and deleting other possible malware that may possible infiltrate system during the time interval you are dealing with system infection on your computer.
Up till now, you have seen how you can manually get rid of adware infection. As you have seen, you have to go through to every possible section on your system such as Applications, Library and to the installed web browsers for suspicious components related to the malicious malware. If you belong to a highly experienced user, you might have no problem in using this manual approach for the malware removal.
However, when we consider the people who are beginner or the less tech savvy who have not much IT skills and have not deal with virus removal steps ever before, the manual adware removal tasks will be difficult for them. Especially for you, we are preparing the automatic malware removal guide. Below, you will see how you can find all suspicious applications on your system by system check using professional tool called “MacKeeper.” The users should use this approach, if they want the removal process to be done in quick and without any hassles. Before we go and understand how to use this software for system scan and remove the suspicious objects, let’s know a little about the software to know what makes software superior than all alternatives.
Special Offer (Macintosh)
Mac users if infected by adware, can try a suggested application to do scan and check if all malicious files and entries are completely removed.
Protect your system and privacy
There are multiple ways how you can protect yourself online. You can use incognito, however, you will be traced even in this mode for advertisements. There is a way to add a protection layer to and cerate complete anonymous web browsing experience using some VPN. These software provide private internet access, reroute through different servers by disguising the IP addresses and geo-locations. Also, these will ensure no data will get recorded, leakage and available to third parties as they follow strict no-log policy. This combination of a secure web browser and VPN will help you browse the internet without being targeted by third parties/ cybercriminals.