In the list of trojans, a new name Honeyhashx86.exe is added recently which can trouble users drastically if the malware somehow gets installed. Trojans are often considered as the most hectic malware form as it allows criminals to do a number of malicious tasks on remote basis, like running some commands, deleting some files, stealing sensitive information and so on. This indicates that Honeyhashx86.exe itself is highly terrible and should be treated in prior. In case if your system got infected by this robust malware code, then you might be experiencing issues throughout the day, and in order to overcome those, we suggest you reading this article.
Being more precise to Honeyhashx86.exe, it’s technically said to be a coin miner trojan, or a specific kind of computer infection that is maximally used by criminals to infect computers and mine digital currencies. This actually uses your computer’s resources like CPU or GPU’s strength to mine cryptocurrency variants like Monero, Bitcoin, Darkcoin, and many more. Based on some reports, this infectious object can utilize more than 70% of your computer resources to do its illicit tasks and obviously the victim users won’t be able to access their machine easily due to lack of resources.
Although, a trojan infections like Honeyhashx86.exe may get installed on computers deceptively and is hidden within system directories, still its impacts can allow users to justify something happened bad with their machine. Actually, whenever they try to access their computers, the applications will stop responding or keep freezing frequently. Also, a number of essential files may seem missing or corrupted leading to throw exe error messages on screen, BSOD errors, and many more. Taking advantage of these, the criminals can easily manage to create a security loophole or backdoor on computer through which more sensitive information can be stolen. To avoid such things, it’s highly suggested to remove Honeyhashx86.exe from compromised computers sooner.
Threat Specifications
Name: Honeyhashx86.exe
Type: Trojan coin miner, spyware
Detected As: Trojan:win32/CoinMiner
Description: Honeyhashx86.exe is discovered to be a new malicious trait that can be termed as a Trojan horse infection that may lead you to suffer high potential losses.
Distribution: Software bundling, intrusive advertisements, redirects to nasty or shady online sources, and so on.
Removal: In order to remove Honeyhashx86.exe from a system, refer to guidelines’ section discussed under this article.
Special Offer (For Windows)
Honeyhashx86.exe can re-install itself if its associated files remain on system somehow. We suggest users to try Spyhunter to check and clean their system against all malicious files completely.
For more information, read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter checks that your computer has malware with its free trial version. If found any threat, it takes 48 hours time for its removal. If you need to eliminate Honeyhashx86.exe instantly, you are required to purchase licensed version of this software.
As mentioned earlier, cyber-criminals have expertise to use some of the services offered by Windows System process as vulnerabilities. They usually mimic a legitimate system process with name of the Trojan or malware. They create the process of a Trojan same as some legitimate system process. In some cases, they easily get differentiated from legit processes however; some cases can be extremely difficult to distinguish.
If you examine the Windows process category in the Task Manager, you would easily notice the legitimate system process. However, if you notice duplicate files process, one must be a malware. This type of Trojan or malware continuously mines bitcoin or other crypto-currencies and this is a very high resource extensive process. The overall speed and performance of the PC gets extremely slow and sluggish. For depth enquiry, you can right click on the doubtful process and choose file location option in order to see the associated program. As a simple rule, if the file is stored in Windows/System32 folder, it is legitimate.
On the other hand, if the process is stored in the user’s processes or “Open the file” for the process leads to any random directories then it is doubtful. You should immediately scan your work-station with a powerful anti-malware tool. Remember that manual removal of harmful process related to Trojan or suspicious files are very difficult due to its deep intrusion and integration with the OS.
How to Remove Honeyhashx86.exe
The first thing that you should do is to scan your work-station with a powerful anti-malware tool and that will be very helpful. On the other hand, if you have backup of your important data in any external clean location such as hard-drive or pen-drive etc. then formatting the infected hard-drive of the PC may also work for you. Remember that formatting the hard-drive may work for one PC but if the infected PC is connected with a network of PCs then this step will go in vain.
Click on the “Download” button to use “SpyHunter” anti-malware tool to clean your workstation.
- On click on the download button, the file named as “Spyhunter-Intaller.exe” gets downloaded.
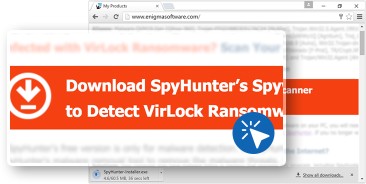
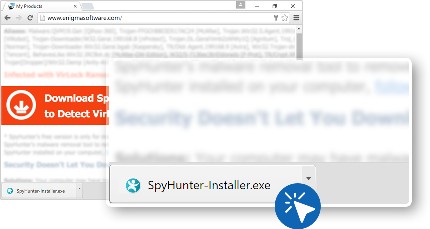
- In the downloads dialog box, choose “SpyHunter Installer.exe” and open the file.
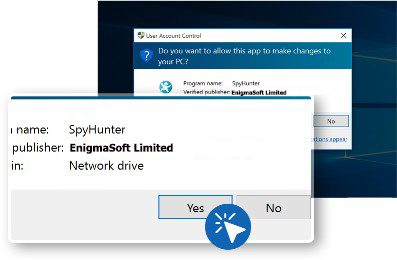
- Select “Yes” in the “User Account Control” dialog box.
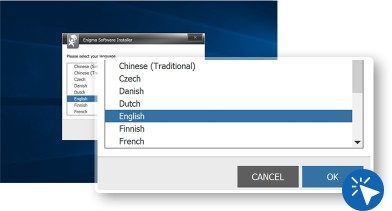
- Select the language you prefer and press on “OK” to get next step
- In order to process the installation, press on “Continue”
- Accept the privacy policy and end user agreement.
- Open “SpyHunter” by locating its icon on the desktop or search it on Windows “Start” menu.
The next step is to use “SpyHunter” for PC scanning and malware removal.
- Go to the “Home tab” and press on “Start Scan” button

Wait for the few minutes to scan gets completed. On completion, it scan result report is presented on the screen.
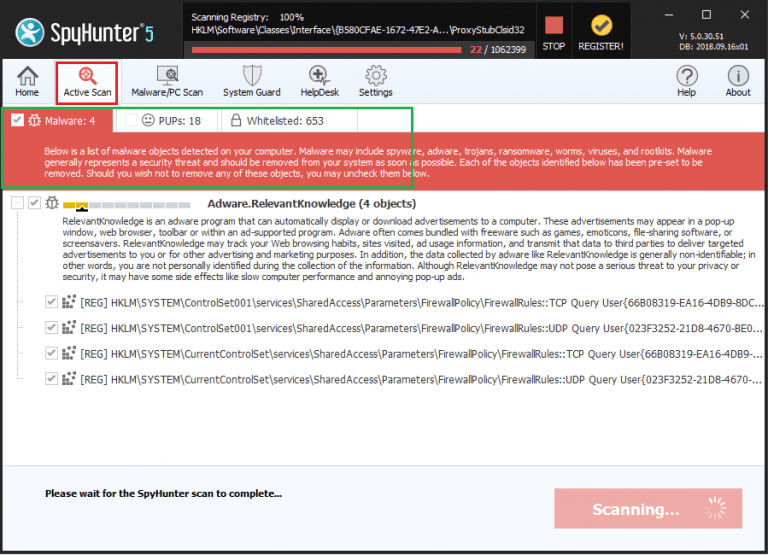
⇒ Register for the Spyhunter and remove Honeyhashx86.exe and all detected threats
To delete Honeyhashx86.exe and all associated threats found through the system scan, you need to register for the SpyHunter:
- Click on the register button available on the top-right corner of the program window,and then click on buy button.
- You will automatically be redirected to the purchasing page, enter your customer detail and valid email address,
- After the successful payment, you will receive email confirmation message. The email contains the account information such as usernames and passwords and so on,
- Thereafter, enter the same detail in the Account tab of the settings section of the program. Now, you can avail full features and protection to your system.
⇒ Steps to remove Honeyhashx86.exe and other detected threats:
Spyhunter antivirus tool categorizes the type of objects detected during system scans in total five sections – “Malware“, “PUPs” (Potentially Unwanted Programs), “Privacy“, “Vulnerabilities“, and “Whitelisted objects“
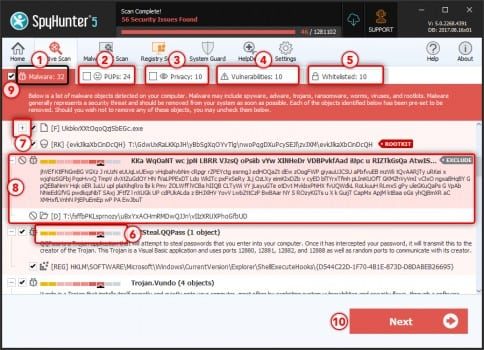
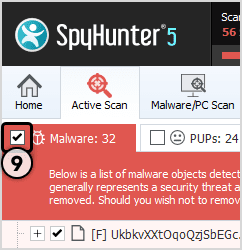
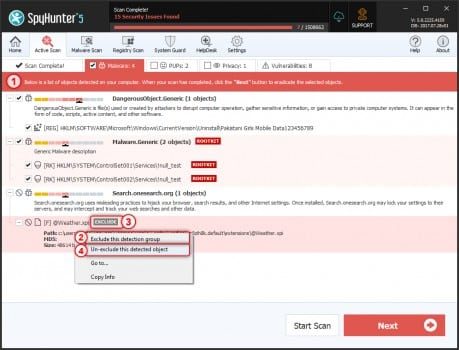
Select the object you want to remove and then click on Next button (you can quarantine an object so that you can anytime restore it to the system using restore feature)
Special Offer (For Windows)
Honeyhashx86.exe can re-install itself if its associated files remain on system somehow. We suggest users to try Spyhunter to check and clean their system against all malicious files completely.
For more information, read SpyHunter’s EULA, Threat Assessment Criteria, and Privacy Policy. Spyhunter checks that your computer has malware with its free trial version. If found any threat, it takes 48 hours time for its removal. If you need to eliminate Honeyhashx86.exe instantly, you are required to purchase licensed version of this software.



